
“MDR, ZTNA, SOAR, IAM”

Charting the Future of Enterprise Security
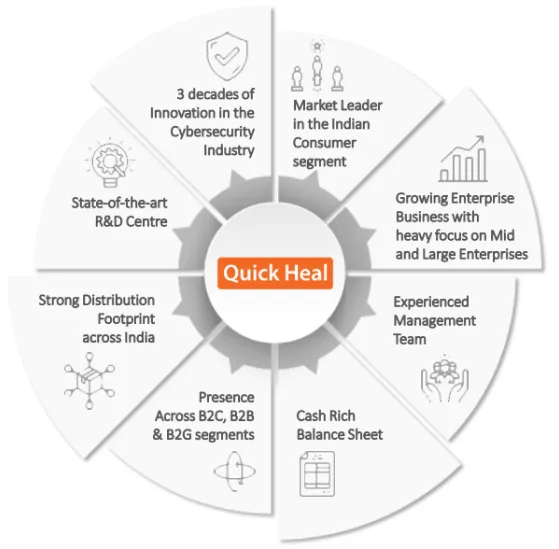
- Collaborators with US Gov (NIST)
- U.S. Artificial Intelligence Safety Institute Consortium Member
- Safest for Banking & Browsing - Recognized
- Pioneer of cybersecurity
- Proud owners of largest malware lab in India
- Protecting 9 Mn active Endpoints
- Granted 8 Patents
- Presence in 76+ countries
- 1000+ Cybersecurity professionals
- Proud partners of ISRO
Trusted Partner for Cybersecurity Transformation
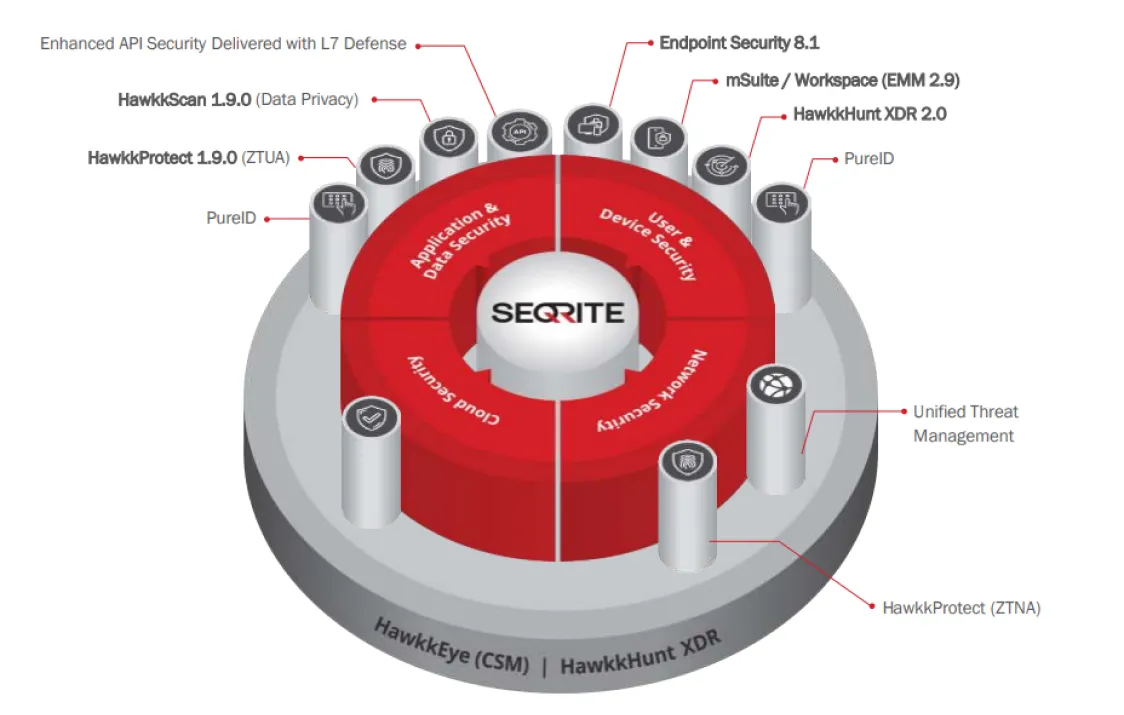
Endpoint Security (EPS) at a Glance

EPS On Premise
- Comprehensive endpoint and data protection in one integrated solution
- Customers: 26K Endpoints: 1.9M

Cloud On Premise
- Comprehensive endpoint and data protection managed from a cloud console
- Customers: 3.9K Endpoints: 220k
Core Protection
- Anti-Malware
- Anti-Ransomware
Network & Web Protection
- Web Filtering, Anti-Phishing, Browsing Protection
- Firewall, IPS/IDS, DDoS, Port Scan
Device Control & DLP
- Advanced Device Control
- Data Loss Prevention
- File Activity Monitor
- Patch Management
Application & Asset Management
- Asset Management
- Application Control
- Vulnerability Scan
Security Compliance and Preparedness
- Endpoint Threat Hunting
- Cloud Sandbox
- File Activity Monitoring
- SIEM integration
Adoption
- Easy Migration from legacy to EPS 8.1
- Easy Migration from 3rd party AV

EPS On Premise
• Comprehensive endpoint and data protection in one integrated solution • Customers: 26K Endpoints: 1.9M


Cloud On Premise
• Comprehensive endpoint and data protection
managed from a cloud console
• Customers: 3.9K Endpoints: 220k

Core Protection
• Anti-Malware
• Anti-Ransomware

Network & Web Protection
• Web Filtering, Anti-Phishing, Browsing Protection
Firewall, IPS/IDS, DDoS, Port Scan
Device Control & DLP
• Advanced Device Control
• Data Loss Prevention
• File Activity Monitor
• Patch Management

Application & Asset Management
• Asset Management
• Application Control
• Vulnerability Scan

Security Compliance and Preparedness
• Endpoint Threat Hunting
• Cloud Sandbox
• File Activity Monitoring
• SIEM integration
Adoption
• Easy Migration from legacy to EPS 8.1
• Easy Migration from 3rd party AV
HawkkHunt XDR solves the customers
Advanced Threat Detection and Response challenges:

Detecting Advanced Stealth Attacks
• MITRE TTP detections using out of box rules
• Rule Builder for custom rules
• Threat Hunting on upto 180 days telemetry data
• ML based Anomaly
• Threat Intelligence based IOC sweep and detection

Single Pane View
• Multi source data correlation – EPS and external systems like firewalls, email etc.
• Investigative Workbench with unified dashboards and drilldowns
• Email and Network alert connectors

Automated Threat Response
• Remediation playbooks – playbook builder
• Automated Response capabilities – granular response functions and checklists
• MDR team for response support

Detecting Advanced Stealth Attacks
• MITRE TTP detections using out of box rules
• Rule Builder for custom rules
• Threat Hunting on upto 180 days telemetry data
• ML based Anomaly
• Threat Intelligence based IOC sweep and detection

Single Pane View
• Multi source data correlation – EPS and external systems like firewalls, email etc.
• Investigative Workbench with unified dashboards and drilldowns
• Email and Network alert connectors

Automated Threat Response
• Remediation playbooks – playbook builder
• Automated Response capabilities – granular response functions and checklists
• MDR team for response support
Our Solutions are Backed by Awards, Certifications, and Patents.
Patented Technologies
USPTO 10,387,649
Signature-less behaviour-based detection technology
USPTO 10,311,234
Anti-Ransomware technology
USPTO 8,973,136
System and method for protecting computer systems from malware attacks
USPTO 8,914,908
A completely automated computer-implemented system and method for piracy control based on update requests
USPTO 8,347,389
System for protecting devices against virus attacks
USPTO 7,945,955
Virus detection in mobile devices having insufficient resources to execute virus detection software Patented Technologies
USPTO 11,216,558
Detecting Malware in Data Streams 470730 Anti-Ransomware
International & ISO Certifications


