“PIM, PAM, DLP”


Collaborating for Innovation and Security Excellence
Arcon Empowering Cybercity Solutions

Identity & Access Management
- Secure access control
- Multi-factor authentication (MFA)

Privileged Access Management
- Monitoring and managing privileged accounts
- Session recording and auditing

Data Security Solutions
- Data loss prevention (DLP)
- Encryption services

Cloud Security
- Secure access for cloud applications
- Compliance management

Identity & Access Management
- Secure access control
- Multi-factor authentication (MFA)

Privileged Access Management
- Monitoring and managing privileged accounts
- Session recording and auditing

Data Security Solutions
- Data loss prevention (DLP)
- Encryption services

Cloud Security
- Secure access for cloud applications
- Compliance management
Key Features
- Innovative Technology: Cutting-edge cybersecurity tools for modern threats
- Compliance Ready: Solutions designed to meet GDPR, PCI- DSS, and other regulations
- User-Centric Approach: Focused on user experience while
EPM Dashboard
Alerts
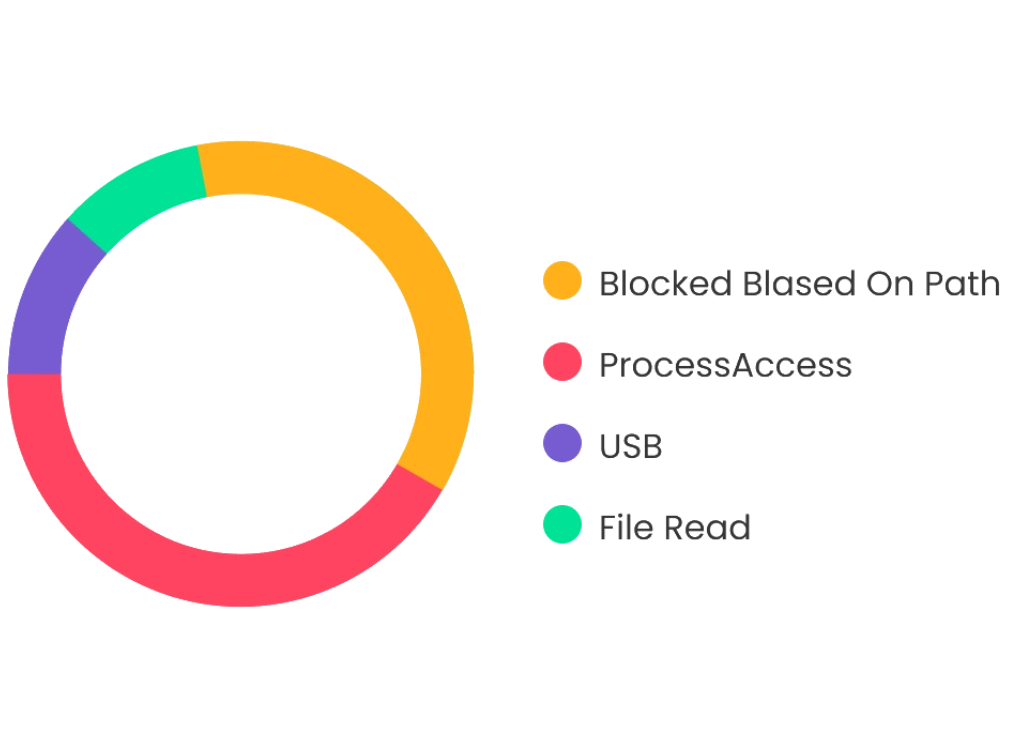
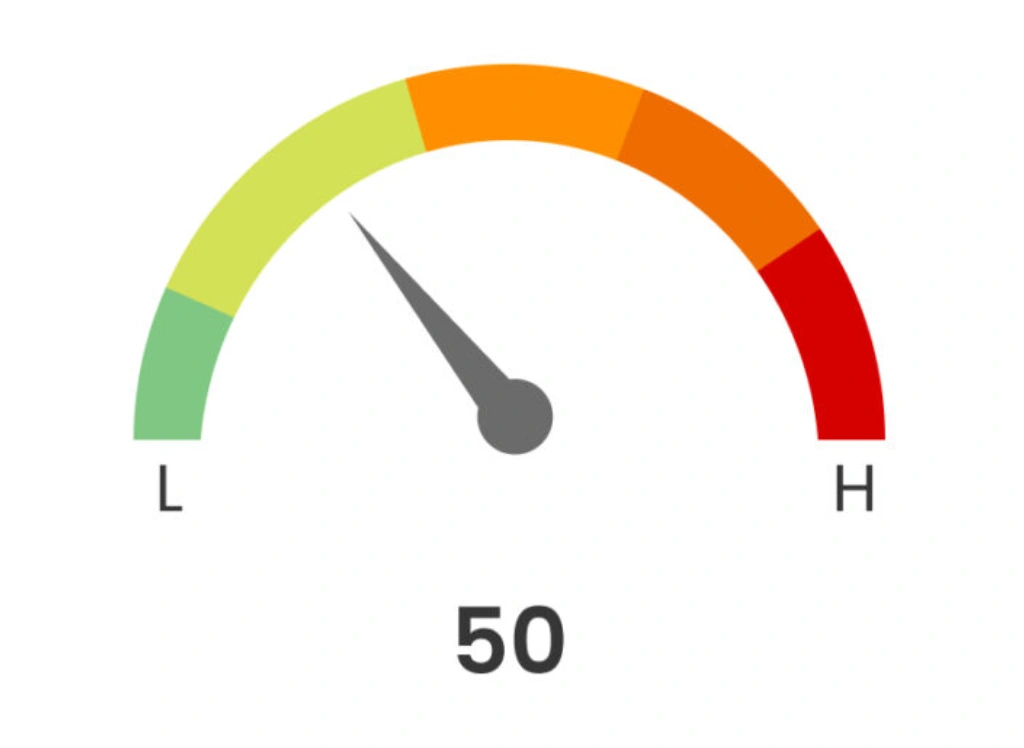
organizational risk
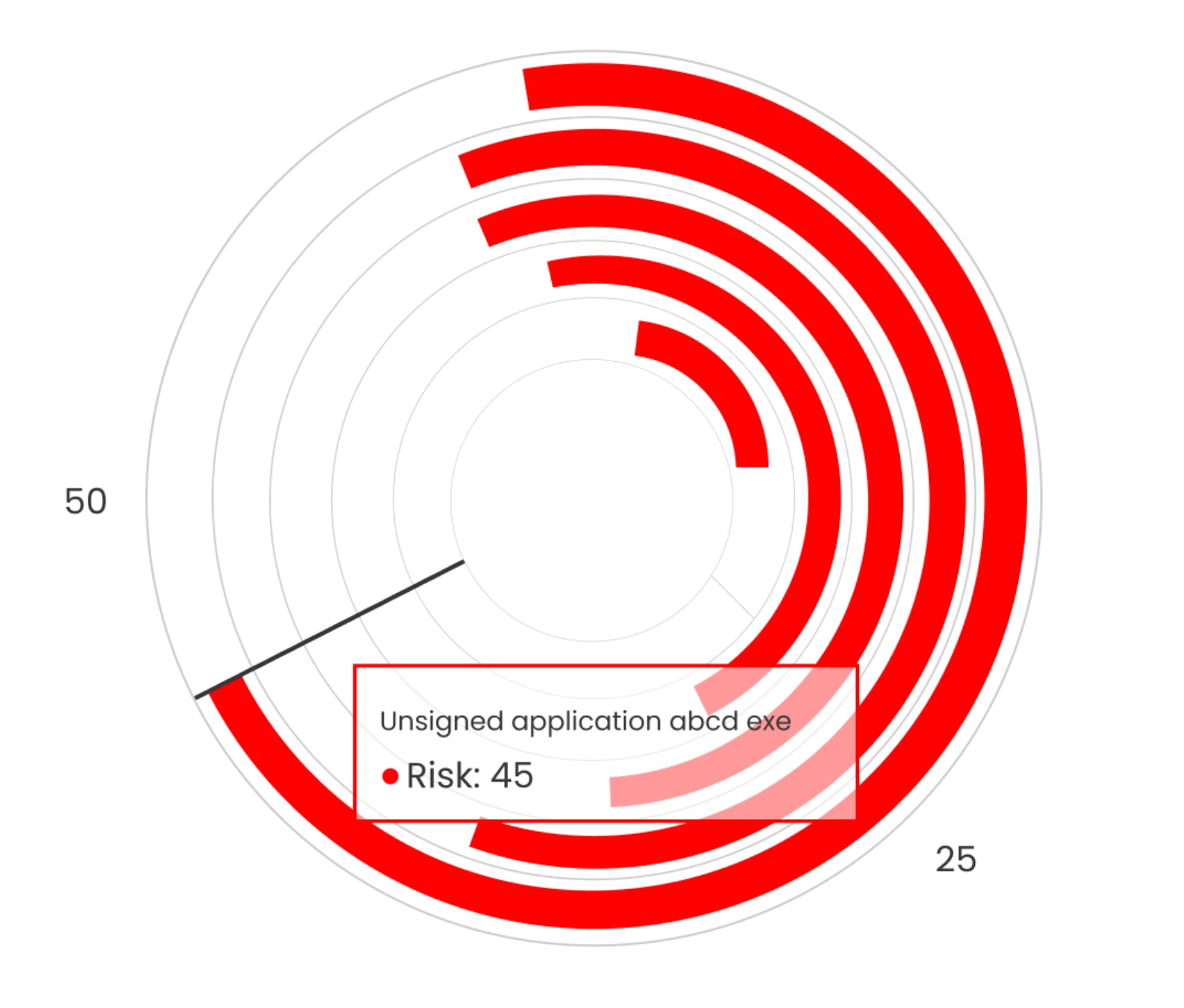
top threats
threats types
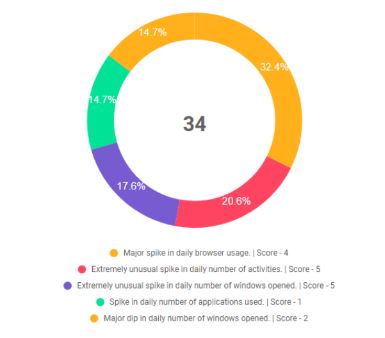
watchlist
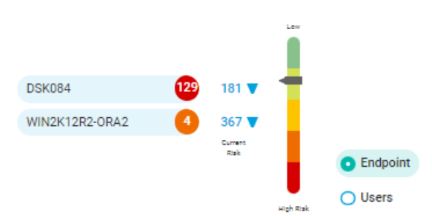
EPM Approach


Monitor
Establish baselines and monitor users, entities, endpoints, applications, and processes over time.

Identify
Detect risky user activity by identifying unusual behavior patterns over time.

Investigate
Investigate suspicious activities within minutes, not days.

Prevent
Reduce risk with real-time user alerts and automated blocking.

Meet compliance regulations
Ensure compliance with key regulations related to insider threats in a streamlined manner.

Investigate
Investigate suspicious activities within minutes, not days.

Identify
Detect risky user activity by identifying unusual behavior patterns over time.

Monitor
Establish baselines and monitor users, entities, endpoints, applications, and processes over time.


Prevent
Reduce risk with real-time user alerts and automated blocking.

Meet compliance regulations
Ensure compliance with key regulations related to insider threats in a streamlined manner.

